A question came up the other day where a customer had the KMS client certificate was about to expire.
The initial client certificate was created with an expiration roughly a year after their encrypted vSAN Cluster installation.
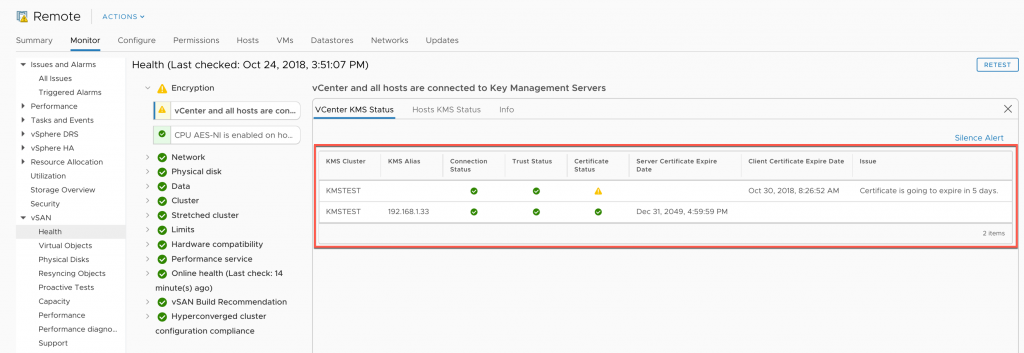
vSAN Health Check
The vSAN Health Check will report on the status of the client certificate each time the health check is run.
Alerts will show up in vCenter, but like any other, can be tied to other actions like an email, SNMP trap, etc.
Notice that the client certificate will expire in a few days.
There is no mechanism to correct this in the vSAN UI, this is because the vCenter to KMS trust, is a vCenter setting, not an individual cluster setting.
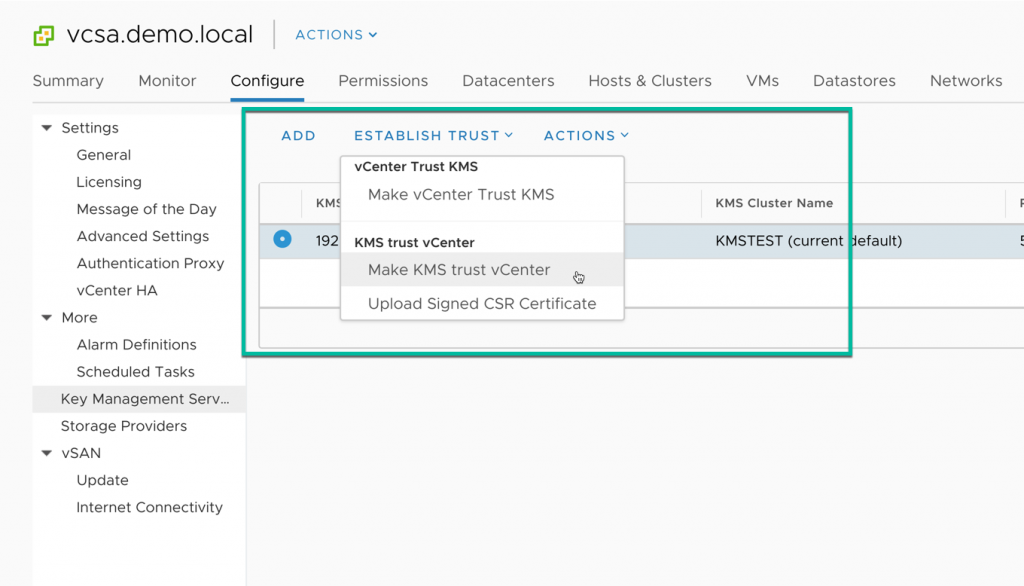
Updating the Client Certificate in vCenter
The process of updating the KMS client certificate in very simple.
Select the vCenter server, and then look for Key Management Servers in the Configure tab for vCenter.
The process up updating the client certificate is the same as the initial process of “Make KMS trust vCenter”
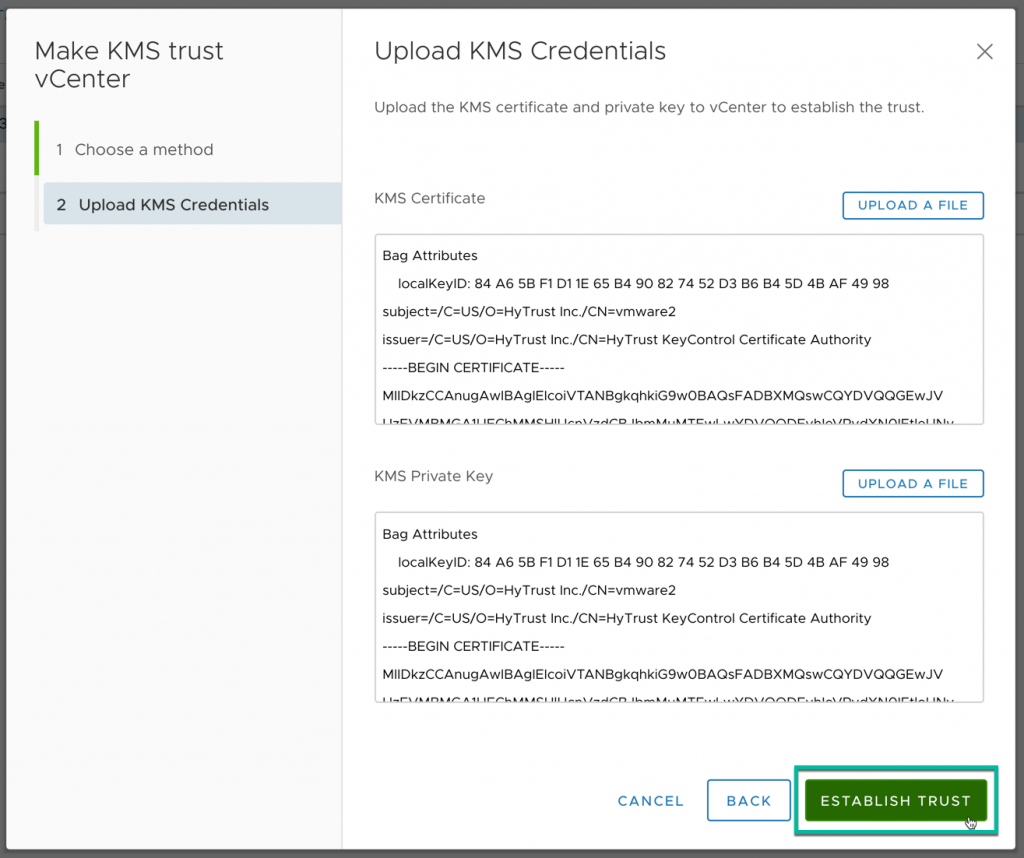
The process of making a KMS trust vCenter will be dependent on the KMS vendor solution that is being used. Using the HyTrust KeyControl appliance, the KMS certificate and private key
Establishing the trust is simple after uploading the new KMS certificate & private key.
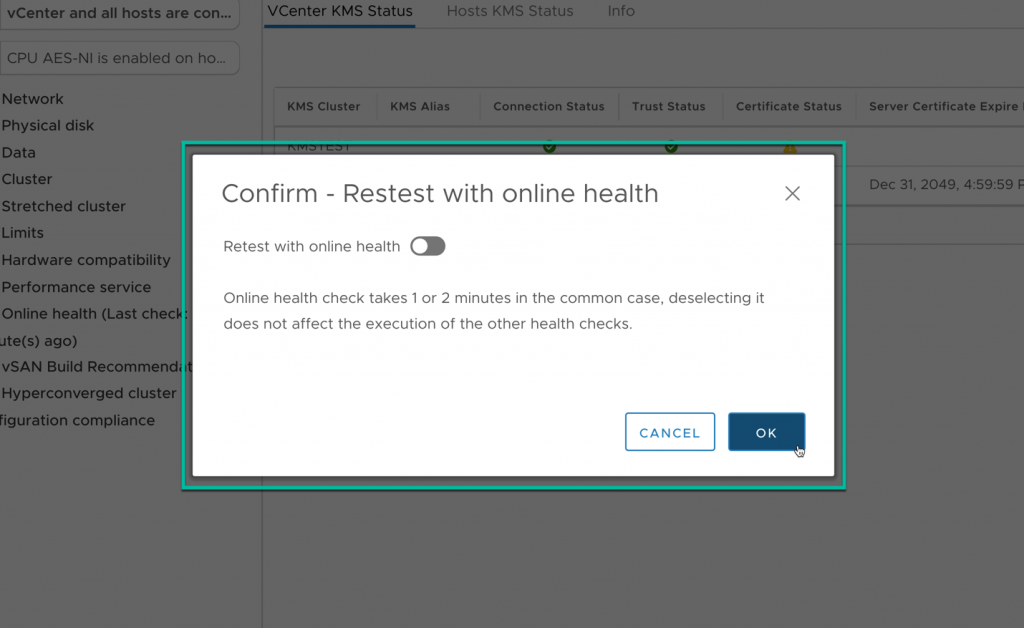
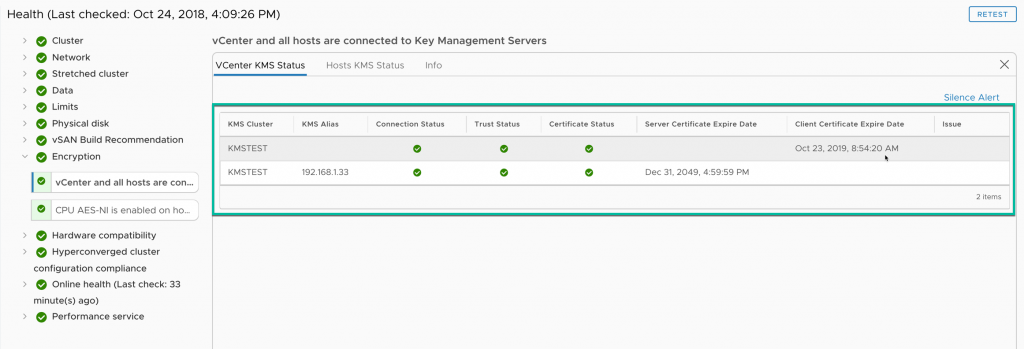
With the new trust established, rerun the vSAN Health Check.
In the green, all good. Five by five.
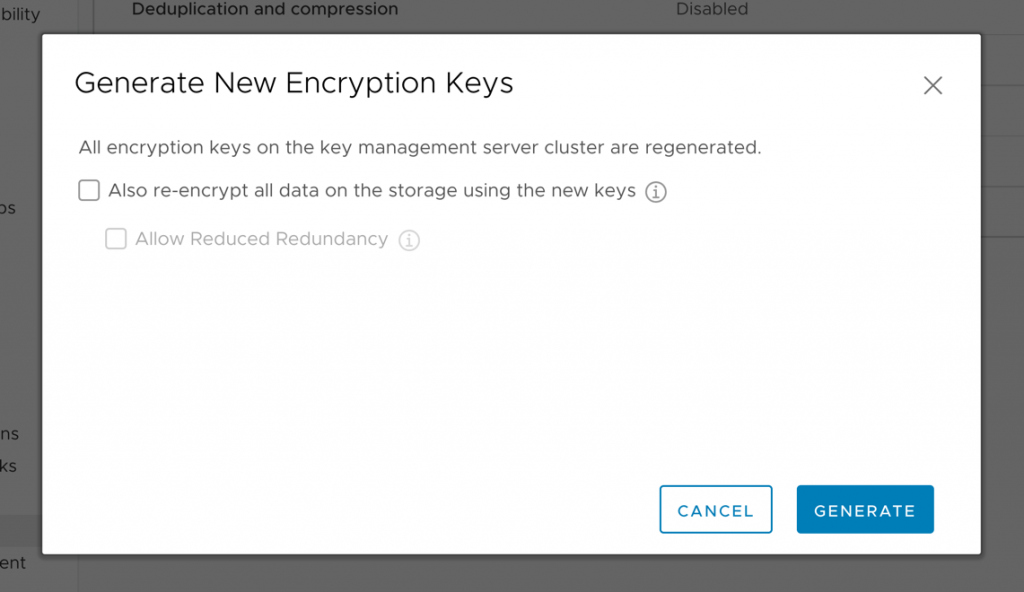
 For good measure, perform a shallow rekey.
For good measure, perform a shallow rekey.
A shallow rekey is non-disruptive, is relatively quick, and can be accomplished quickly and easily.
Summary
Even though the process to update the client certificate is relatively simple, it isn’t something that should be taken lightly.
Encrypted vSAN clusters will continue to run once the Host Key and Key Encryption Key (KEK) are loaded. A client certificate could expire, and hosts would still have encrypted disks mounted. Should one of those hosts reboot, with an expired client certificate, they would not be able to mount the encrypted vSAN disks.
Make certain the KMS client certificate is valid and hasn’t expired to keep your encrypted vSAN cluster healthy and happy.
This was originally posted on the VMware Virtual Blocks site: https://blogs.vmware.com/virtualblocks/2018/10/25/ve-client-cert-update/