Welcome to the #StorageMinute series where we deliver key topics via bite-size content. In this edition, we will take a look at Key Rotation in vSAN Encryption.

Keys for Security
Keys are required to open locks and access the contents that are secured. Different locking mechanisms require different types of keys. These keys could be physical or virtual/digital.
Keys really don’t have any value if they can be circumvented easily or are commonly known.
Looking closer at this image of a combination lock on a safe, we can see that the lock will not do anything to prevent access to the contents inside the safe. This is because the combination is readily available in the same proximity as the lock itself. Removing the tape with the code will restore “some” security, but will only prevent those that do not already know the combination.
In situations where keys could be compromised, a proper key rotation strategy ensures that only authorized parties have the correct keys.
Key Expiration & Rotation
Hotels expire keys after a guest spends the night. Businesses deactivate badges when an employee leaves for another company. Those are good examples of key expiration, but for individual stakeholders.
Landlords changing locks after tenants move out, is a good example of rekeying. The landlord still owns the property, but changes out the locks.
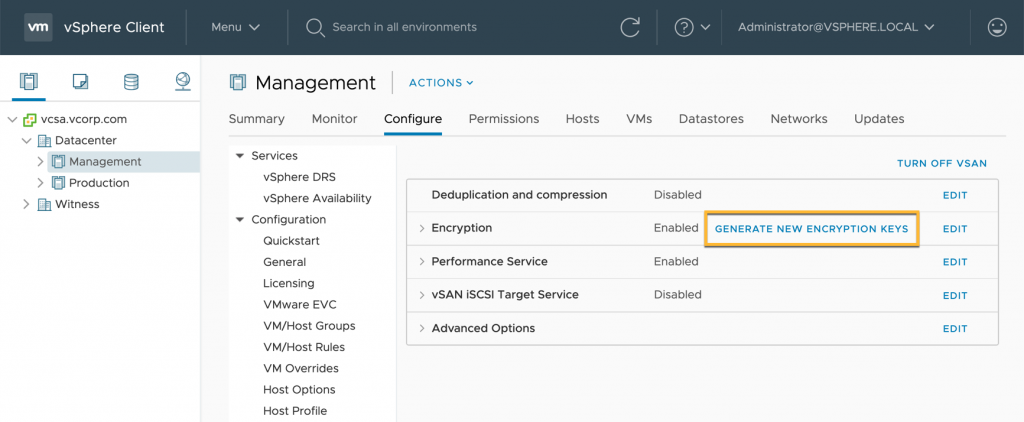
Changing out physical locks are can be costly and time consuming. And while rekeying storage typically is not as difficult or time consuming, some element managers don’t make it the easiest task to perform. Generating new encryption keys can be accomplished easily in the vSAN Configuration UI with a few clicks.
We can easily perform either a shallow rekey or a deep rekey from the vSAN Configuration UI.
A shallow rekey is quick and easy, only changing the Key Encryption Key (KEK) which is used to wrap the Data Encryption Key (DEK) location on each vSAN storage device. A deep rekey process takes longer as each disk group is evacuates data to other available cluster nodes*, and then the disk group is recreated with a new DEK on each storage device. Both rekey operations can be performed without having to shutdown the cluster or the VMs running on vSAN. *2 & 3 Node vSAN requires reduced redundancy to perform the rolling rekey process.
In the video we will show you just how easy it is to perform either a shallow rekey or a deep rekey.
The rekeying process can also be called by API or PowerCLI for customers that wish to better automate the process.
Key Takeaways
It is a common strategy for customers to rotate keys to encrypted system. vSAN makes the key rotation process easy & painless.
- Shallow rekeying is very quick & does not move any data
- Deep rekeying is more time consuming, requiring data movement within the cluster
- Can be easily performed in the UI or by API/PowerCLI
- VMware recommends key rotation intervals that align with business guidelines
References
- VMware Docs – How vSAN Encryption Works
- StorageHub – vSAN Data Encryption at Rest Tech Note
- VMware Code – vSAN Encryption PowerCLI Rekey Example
- VMware Code – vSAN Encryption PowerCLI Sample Report
This was originally posted on the VMware Virtual Blocks site: https://blogs.vmware.com/virtualblocks/2019/04/08/storageminute-vsan-encryption-and-key-rotation/